Information leaks are deadly for all categories of business, especially health care, government agencies and non-profit organisations. Overall, the average cost of a data breach increased from $3.6 million in 2018 to $3.92 million in 2019 globally. The USA has the highest country average breach cost which is equal to $8.2 million, according to the IBM Cost of a Data Breach Report 2019.
What has been done to protect information (in vain)
Businesses are accustomed to relying on external perimeter security: various DLP-systems, firewalls, session border controllers etc., ignoring or weakly controlling the internal workflow. Employees, especially middle management positions, are left to their own: could bring their own devices to work, could freely print documents, could work remotely and borrow copies of documents home.
Individuals usually rely on in-built security mechanisms, like setting permissions and using copy-protected PDFs. They tend to forget which documents are shared with whom and have to occasionally review permissions.
Unfortunately, in all cases where data breaches were an inside job, the access control and perimeter protection has not yet done any good, as seen from the statistics above.
The perpetrator already exists within the secured perimeter and has surprisingly high chances to pass it with a photo of a financial statement saved on his or her smartphone.
As it became clear for us during hundreds of employee interviews, internal perpetrators assess their information security awareness in the company as “good” or “great” in more than 70% cases. This is why you need an additional layer, which:
✓ Eliminates anonymity and impunity when working with sensitive documents
✓ Does not use plain protection techniques to eliminate the desire to deceive it
✓ Unmistakably identifies the source of the leak
✓ Transparently integrates into existing business processes
✓ Identifies who was printed or photographed the document
✓ Works with the variety of file formats
✓ Does not require complex maintenance
Businesses and individuals sometimes use forensic technologies, like watermarking, microdots or custom fonts to protect their sensitive documents and track the perpetrator to the exact person. These tools (and many others) utilise steganography as their core technology.
Real solution: part 1
The workflow is as follows: the tool generates a unique copy for each recipient, integrating all the document meta into the body text and vice versa — uses its algorithm to determine the exact owner, company, timestamps etc.
This technology looks promising, while hows and whys increase the level of protection, but they do not solve the problem fundamentally, since almost all of them:
1. Visible, which makes it easy to identify unprotected documents and steal them.
2. Often unable to determine the source of the leak by document fragment, which appears in the web more often rather than the original.
3. Cannot produce unlimited copies.
Try out LeaksID, our latest solution to protect your sensitive documents from leakage made with hard copy, photo or a snapshot.
Part 2. Introducing LeaksID proprietary algorithm
Start working with LeaksID by adding sensible documents one by one or in bulk, and setting up a file hierarchy. The system will recognize, protect and save each document. It would be enough to determine the exact name of the person responsible for the leak, timestamp and location.
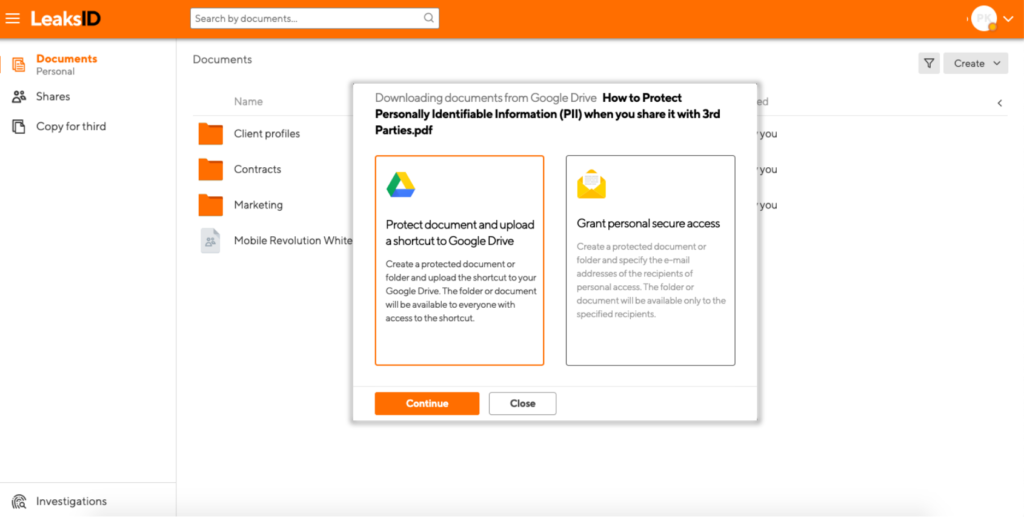
Share documents securely by creating one-time Google Drive shortcuts, sharing permanent links via email and assign permissions for each separate set of recipients.
If you ever come across a leaked document, conduct an investigation: upload the leaked document copy sample and set up a few anchors to help the system recognize it. Launch an auto-investigation or tweak the investigation process manually and identify the perpetrator in just a few minutes.
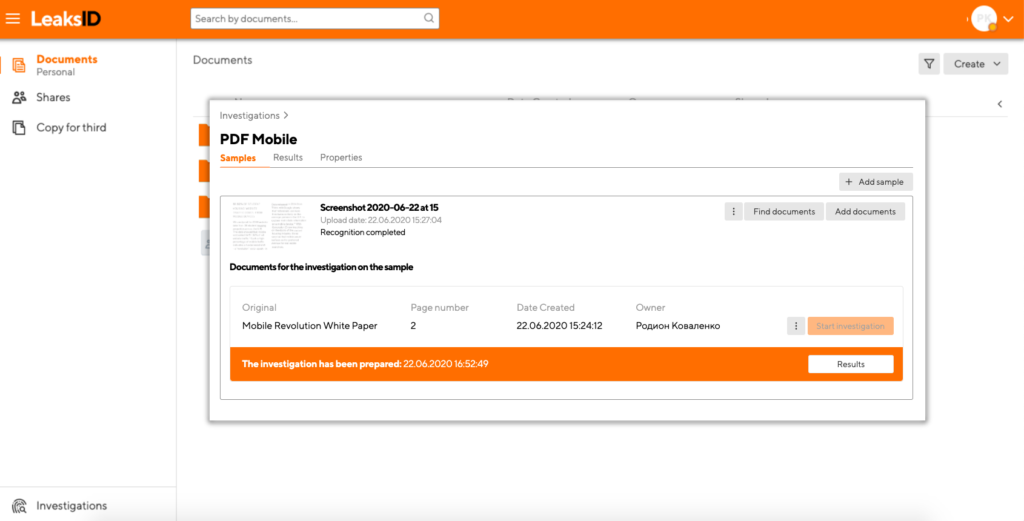
With the help of its algorithm LeaksID is able to find the source, even if the leaked copy is damaged, shot from an angle or contains only a paragraph from the original copy.
Try LeaksID once it is online!
The project development is currently in progress, and we are expecting LeaksID release this week. However you can sign up for updates using the official LeaksID website, so we will notify you once the product is ready by email.
We’ve also decided to give the first 100 registered users an additional free trial month so that you can better evaluate the application and leave a constructive feedback.
Try out LeaksID, our latest solution to protect your sensitive documents from leakage made with hard copy, photo or a snapshot.


















































