Watermarking has long been used as a method to protect digital content from unauthorized use and distribution. However, traditional visible watermarks have certain limitations and can be easily removed or tampered with using photo editing tools. In contrast, LeaksID offers an innovative solution with its anti-leak labels or fingerprints that are completely invisible to the naked eye.
The key difference - invisibility
The key difference of LeaksID’s invisible marking lies in its imperceptibility, unlike traditional visible watermarks. LeaksID’s labeling, known as anti-leak labels/marks or fingerprints, operates on a steganographic approach, making hidden modifications that are not visible to the naked eye. This technology allows for the creation of over trillions of copies for a single document page. Consequently, organizations with large document flows can easily create copies without any hassle, ensuring that each employee receives an individualized copy tailored specifically for them. Moreover, LeaksID’s invisible marking is not limited to digital versions of documents; it also remains intact on printed copies. This means that even if a printed copy is leaked or photographed, the marking will still be present, enabling investigations to detect the source of the leak.
When comparing visible watermarks to LeaksID’s labeling, there are several noteworthy advantages of LeaksID. Firstly, visible watermarks can be erased using various photo editing software, while LeaksID’s marking cannot be detected by the naked eye. Secondly, visible watermarks sometimes cover parts of the document content, making it difficult to read. In contrast, LeaksID’s invisible marking does not obstruct the document, allowing employees to continue working seamlessly without any hindrance. Additionally, when integrating LeaksID on-premises, the integration process is seamless and transparent.
Collaborating for Document Security: Visible Watermarks and LeaksID's Labeling Unite to Achieve One Goal
Both visible watermarks and LeaksID’s labeling share the common goal of preventing potential leaks and deterring individuals handling confidential documents from engaging in unauthorized actions. For instance, visible watermarks contain information indicating the document’s confidentiality, advising against any further action. Similarly, LeaksID’s marking serves as a reminder, making employees aware that all documents within the company are marked, discouraging unauthorized actions that could disrupt the prescribed document handling processes. Moreover, it’s worth noting that visible watermarks and LeaksID’s labeling can work together, complementing each other’s functionality. By combining both visible watermarks and LeaksID’s invisible fingerprints, a more comprehensive approach to protection can be achieved. In such cases, a single watermark can communicate that the document is protected invisibly by LeaksID, further emphasizing that no action should be taken with the document.
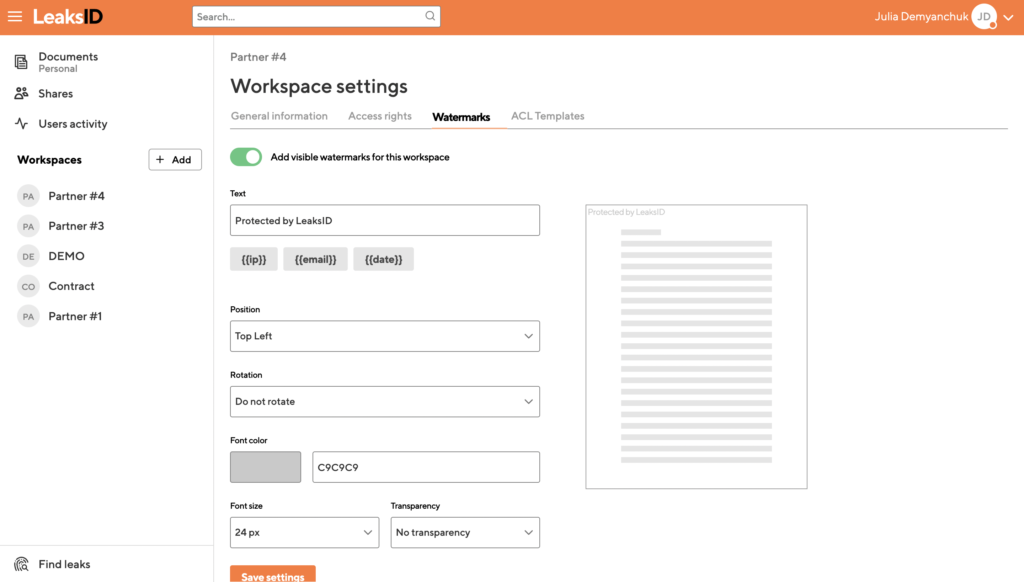
In our SaaS solution, we have even incorporated visible watermarks, allowing users to manually add them to already marked documents using our invisible fingerprint labels. This enables a flexible approach to document protection, catering to different requirements and preferences.
Conclusion
In conclusion, while visible watermarks have been widely used for content protection, LeaksID’s anti-leak labels introduce a new level of security through invisible markings. LeaksID’s invisible fingerprints cannot be easily removed or detected, making them an effective solution for safeguarding digital and printed documents. By combining the strengths of visible watermarks and LeaksID’s labeling, organizations can adopt a holistic approach to document protection, ensuring comprehensive security and reducing the risk of insider threat.



















































