G-71 Inc. is thrilled to announce that its patented flagship product, LeaksID, has been recognized as a High Performer by G2 in the Spring 2023 G2 Grid® Report for the Cloud File Security category. This recognition is a testament to G-71’s commitment to providing a comprehensive solution that helps organizations protect sensitive files, documents, and information from insider threats. This is an incredible achievement for us which was made possible thanks to our customers and their precious reviews.
What is LeaksID?
LeaksID is a cutting-edge ITM (Insider Threat Management) solution by G-71 Inc. that deters sensitive documents from insider threats. The solution utilizes a patented algorithm and a steganographic approach to embed unique, undetectable anti-leak marks into confidential documents, effectively deterring data breaches. LeaksID is equipped with invisible markings that can identify the source of a leak, including the responsible party’s name, even if the document was compromised in the form of a photo or screenshot. This enables organizations to quickly identify and address any security breaches, making LeaksID an indispensable tool for businesses that deal with sensitive and classified information.
LeaksID offers clients a versatile deployment model that encompasses a cloud-based format. Its cloud-based approach is simple to integrate and guarantees a seamless user experience, providing clients with a sense of security and peace of mind. In the cloud infrastructure, LeaksID can act as a file storage solution for confidential documents and as a data room for sharing them with external users. It can also be linked with Microsoft Exchange to label attachments in emails. Furthermore, it can be utilized as a Web Application Firewall when interacting with web-oriented applications such as OneDrive or Google Drive.
What is G2?
G2 is a platform that enables professionals to assess the various software options available in the market through peer-to-peer reviews. By providing in-depth and unbiased evaluations, G2 is a dependable source of objective feedback regarding software.
To determine product rankings, the G2 algorithm considers multiple metrics, including customer satisfaction, market presence, and market leadership. Customer satisfaction ratings and reviews are used to calculate the customer satisfaction score, while the market presence score is calculated using factors such as market share, vendor size, and social impact. Lastly, the market leadership score is calculated based on elements such as product adoption, brand awareness, and customer satisfaction. G2 then utilizes this data to assign scores for the Grid report.
At the moment, we have over 10 reviews on the G2 website with an average rating of 4.7 out of 5. This motivates us to continue developing our product that meets the needs of our target audience. We hope that in the next G2 report, we will receive even more badges, not only in the Cloud Security category but also in the two other categories that we actively promote on G2 - Data Loss Prevention (DLP) Software and Insider Threat Management (ITM) Software.
Julia Doronina, G-71 CMO
The G2 Grid presents a graphic display of software solutions’ scores and rankings within a specific category. Divided into four quadrants, namely Leaders, High Performers, Contenders, and Niche Players, the G2 Grid positions the software solution based on its score.
LeaksID as a G2 High Performer
In the Spring 2023 G2 Grid® Reports, LeaksID received two badges connected with its cloud-based options. The first badge was the G2 High Performer badge in the Cloud File Security category, and the second badge was the G2 High Performer Small-Business badge in the Cloud Security category.

The G2 High Performer badge in the Cloud File Security category signifies that LeaksID is one of the top-performing software solutions in the market. It indicates that LeaksID has high customer satisfaction scores and meets the needs of users efficiently. The G2 High Performer Small-Business badge in the Cloud Security category is a testament to LeaksID’s ability to cater to the needs of small and medium-sized businesses.
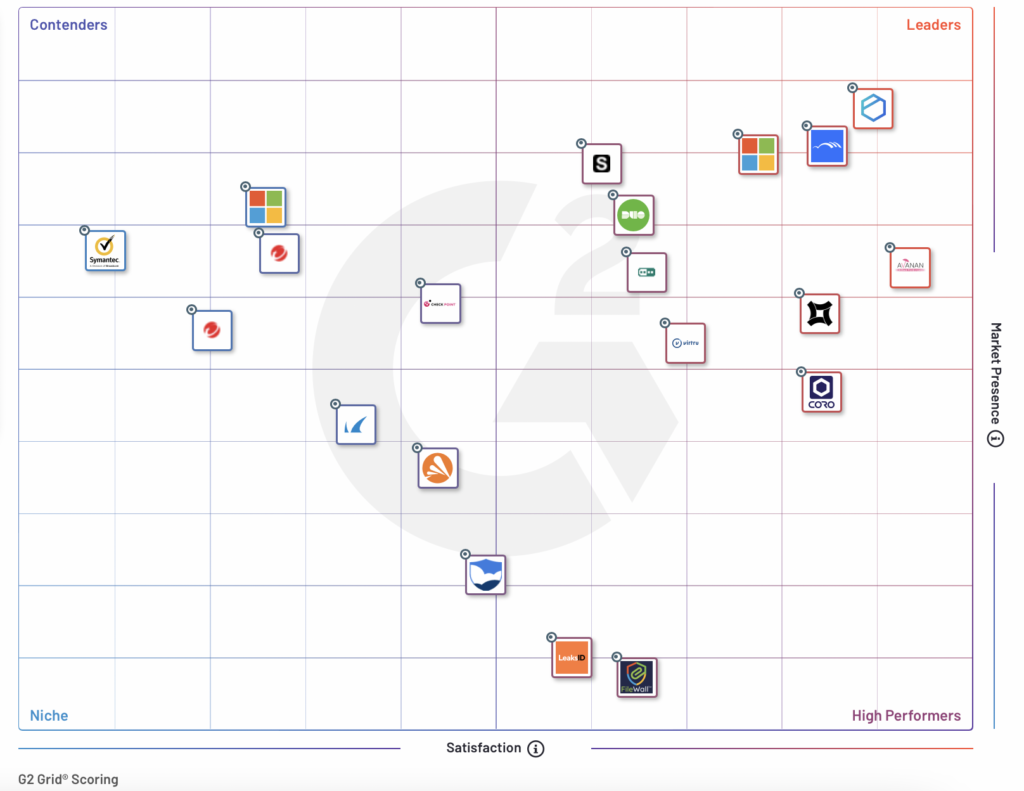
We are proud to be recognized by G2 as a High Performer, and we could not have achieved this without the support of our customers, who have provided us with valuable feedback that has helped us improve our product. We will continue to provide exceptional software solutions to our clients and work towards achieving greater heights.
Sergey Voynov, G-71 CEO and Co-Founder



















































