There are a lot of interesting statistics in the 2022 Cost of Insider Threats Global Report by Ponemon Instutute; but let’s pay attention to the next section: frequency of insider-related incidents per company.
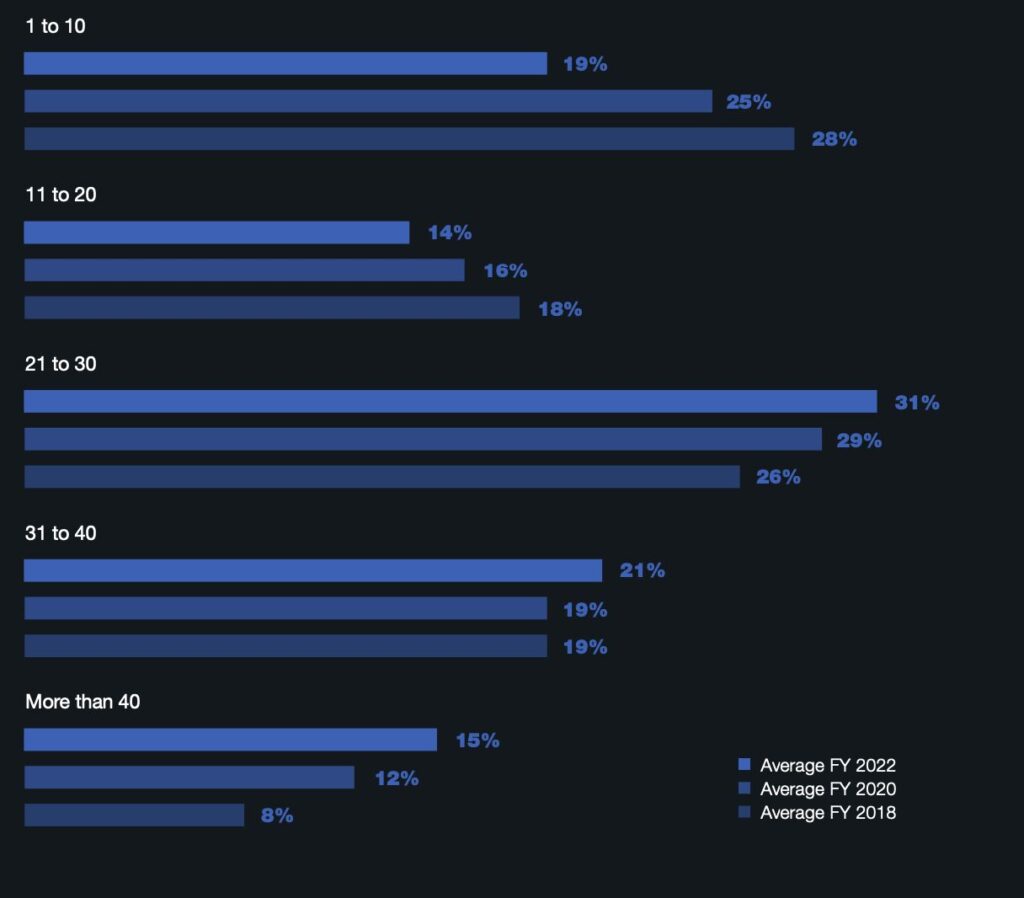
The image below shows the average consolidated frequency of employee/contractor negligence, criminal/malicious insider and credential theft incidents per company. According to the 2022 research, 67 percent of companies experience between 21 and more than 40 incidents per year. And the cost of a single incident can be more than $500,000.
That should make it crystal-clear that companies’ existing protection systems cannot cope: new and innovative approaches are needed. One of them is introducing preventive protection by invisible marking of documents using the LeaksID method. If everyone knows that all confidential documents in the company are marked, then the desire to compromise such a document will decrease, since the inevitability of punishment will loom large.
Try out LeaksID, our cloud solution to store documents, collaborate on them, and securely share them.