In the event of a data breach, including insider leaks, a company must take a number of necessary actions as part of a quick response to the situation, and also spend a lot of money on the consequences of the leak. One of the costs associated with a company’s response to insider-related incidents is related to performing the investigation. In this article, we will tell you what an investigation is and how LeaksID can help with it.

What is a Data Breach?
A data breach is an event that entails the disclosure of confidential and protected information to an unauthorized person or persons. Such a breach can result in financial loss, legal liability, and reputational damage. Therefore, when a data breach occurs, it is necessary to immediately take several measures to eliminate and prevent it.
Cost Activity Centers Connected with Data Breaches
According to the Ponemon Institute’s 2022 Cost of Insider Threats Global Report, there exist 7 cost activity centers connected with data breaches:
1. Monitoring and surveillance: These are activities that enable an organization to ensure early detection and deter potential leaks.
2. Investigation: Actions required to determine the source and extent of the incident
3. Escalation: Activities taken to raise awareness of real incidents among key stakeholders within the company.
4. Incident response: Activities relating to the formation and engagement of the incident response team.
5. Containment: Activities that focus on stopping or lessening the severity of insider incidents.
6. Ex-post response: Activities to help the organization minimize potential future
insider-related incidents.
7. Remediation: Activities associated with repairing and remediating the organization’s systems and core business processes.
The cost for each direction within a single leak is a total of $645,997, which is 84% more than in 2016, 25% more than in 2018, and 1% more than in 2020. If we consider each direction separately, then the costs are as follows:
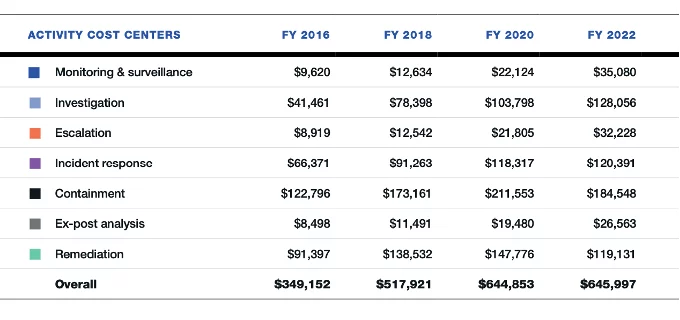
It can be seen from the statistics that the Investigation section accounts for the second largest expense after Containment, and in 2022, it amounts to $128,056 per leak.
Difficulties in the Investigation
A key part of the investigation is to detect the data breach and find the source of the leak. To do this, the company collects extensive information about the leak itself and attempts to determine who is responsible for it.
Sometimes, it is difficult enough to quickly determine the source and who is guilty of disclosing confidential information. The fact that sometimes attackers simply take photos of confidential documents on their own smartphone and publish them online aggravates the situation. It is very difficult to quickly detect who did it.
But what if all documents had some kind of “traces” in advance, using which it would be easy to determine who took a photo or screenshot with sensitive information?
When investigating, data from DLP systems installed in many companies can be of great help. But they are powerless if a photo was taken on an external device. This is where LeaksID can help.
LeaksID Investigation Module
Thanks to the invisible LeaksID markings applied to all documents when working with them (read more about markings here), you can find out the source of the leak in a matter of minutes. To do this, you just need to upload a fragment of a compromised document to the LeaksID investigation module, and the system will automatically determine the owner of the copy.
There are several types of document leaks, on which LeaksID will perform a full investigation and identify the leak source, namely: a screenshot, a photocopy or scanned copy, a photo of a printed document, and a photo of a document opened on a screen. There is an individual approach to the investigation methods for each of these leak types, and depending on the quality of the existing sample.
LeaksID doesn’t require the whole document to carry out the investigation, but only a small part of it. If you have a fragment of the document labeled earlier with only several lines of text or several blocks of words (3 for each line), LeaksID can work with such a fragment. A simple principle is applied here: if you can visually recognize the text in the available fragment, the system can recognize it as well.
After the investigation, the system will return a result with the assumed name of the owner of the compromised copy, and it will show the version of the document that was compromised. With this information, the organization will understand which version was used and who had access to it last. Using this data, the investigation can be carried out several times faster and more cost-effectively.
At its core, LeaksID prevents future leaks by creating a preventive effect through labeling and leak investigations, thus making security officers’ work easier.
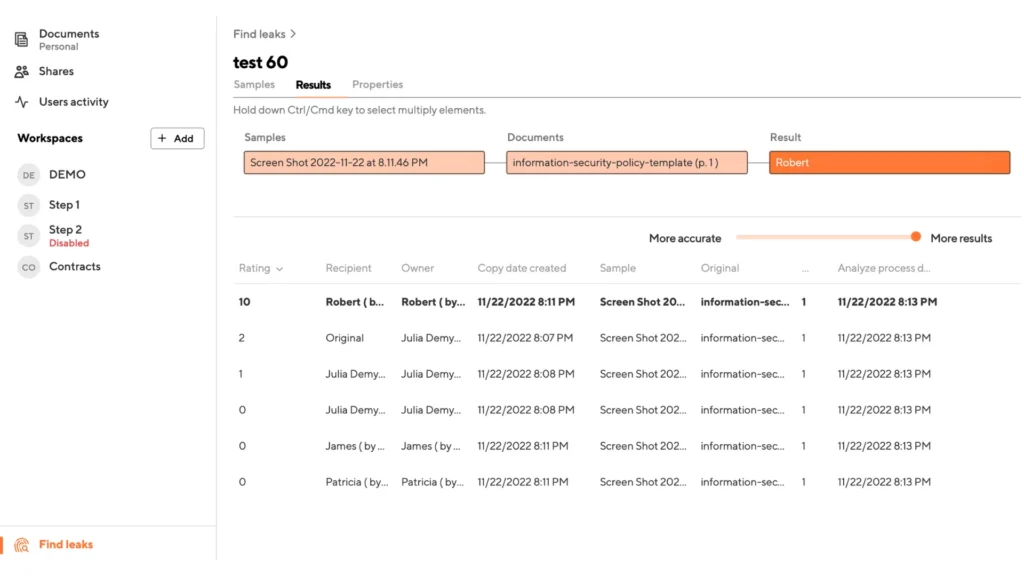
For example, in the screenshot below, you can see that the system highlighted Robert’s name and gave them a rating of 10, saying that they are the owner of the compromised copy and most likely they compromised it (not counting the possibility that someone specially did something under their account name).
Try out LeaksID, our cloud solution to store documents, collaborate on them, and securely share them.