Heightened document security
Protect sensitive Text Data with LeaksID Data Room
Improve the security of your sensitive text data by incorporating an invisible fingerprint, which can help prevent leaks and add an extra layer of protection while working with documents and sharing them via the data room.









LeaksID Data Room as an Insider Threat Management Tool
LeaksID offers a comprehensive package that provides a wide range of options, including a data room to store sensitive documents, exchange them, and conduct investigations in the event of a leak.
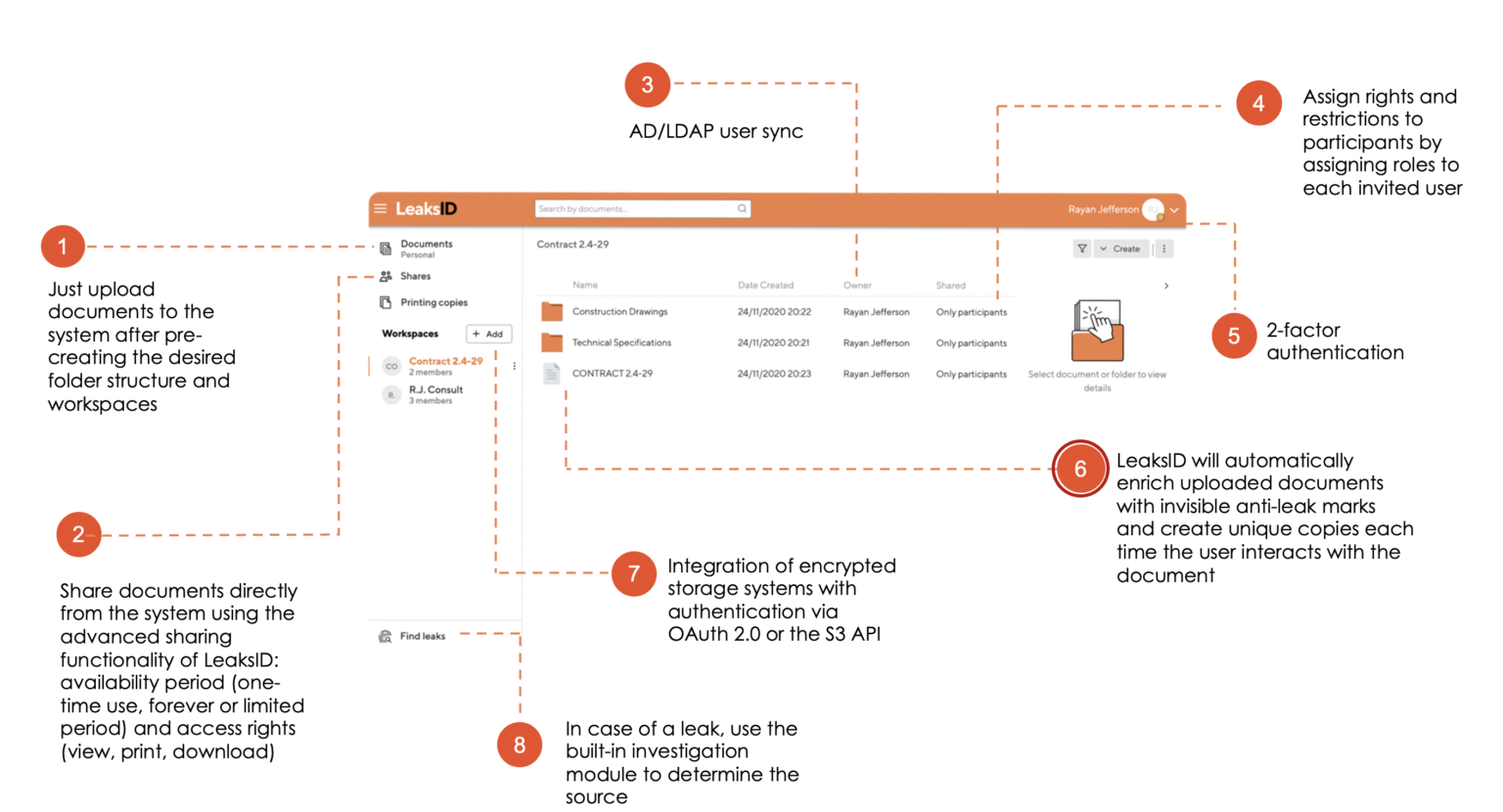
Registering with LeaksID takes no more than a minute and is suitable for teams of any size.
With each interaction inside the data room, invisible fingerprints are automatically integrated into every text document.
In addition to its preventive effect in deterring leaks, LeaksID offers an integrated module for investigating leaks.
Explore a wide range of integration possibilities, whether it’s in the cloud or on premises.
What is LeaksID?
The LeaksID Data Room is specifically designed to safeguard sensitive files from internal threats, providing a comprehensive steganographic method to seamlessly embed invisible fingerprints within confidential documents as you work with them.
Such marking creates a preventive effect, both within your company, and when working with third parties, to reduce the number of leaks of sensitive materials.
If a leak does occur, wherein someone takes a photo of a document or captures a screenshot, you can utilize the built-in investigation module to identify the source of the leak by analyzing the leaked fragment.
Reduce the risk of insider threats. Find the culprit in case of a leak.
The system supports various document formats, including doc(x), pdf, ppt(x), jpeg, png, CAD, etc.
LeaksID marks can’t be detected or removed without our specialized tools, unlike visible watermarks
Utilize LeaksID to securely exchange sensitive documents directly from the system, both within your team and with third parties.
It doesn’t matter how documents were leaked: as photos, screenshots, printed copies, etc.
Reduces insider threats for any type of business
Approximately 75% of leaks originate from individuals who possess legitimate access
to document handling and exchange, but
compromise the document’s security by capturing a photo or screenshot.
Deter potential leaks with LeaksID
of each organization
Our intuitive SaaS
application
Deploy immediately to start marking your confidential documents and deterring leaks.
Our flexible and powerful
enterprise solution
Integrate our invisible fingerprint technology into your system and solutions via API or proxy server.
A deterrence technology
for any type of business
Reviews

Cristian Toba
Chief Solutions Architect
Even though hidden watermarks to prevent unauthorized copying is an old idea, it’s the first consumer oriented product that I see.

Yulai
UX/UI Designer
Really protect docs and you can share document securely from the system.

Nishith
Founder
Indispensable tool for companies and individuals to store sensitive data.

Dawn Veltri
Director of Marketing
Sharing our documents just got easier with LeaksID. The function of tracking activity with each document will help a lot to understand whether the recipient has opened it or not.

Pierre Kraus
Business Analyst
Very innovative! It’s very helpful to be able to protect & track your online documents to better control your data.

Vit McFly
Consulting
Leaksid tends to be a primary solution when I need to share private docs.
Security
Your data is securely stored using Amazon Web Services in the US. Our app has been verified by Google and Stripe.
Security Management Controls
Personal Data Protection

Security, Availability, and Confidentiality Report

Cloud Security Alliance Controls




