Over the past years, the number of leaks of confidential documents, trade secrets, and intellectual property has been on the rise. Statista shows that the number of data breaches in the U.S. has significantly increased, by 51% within the past decade.
The global threat intelligence market is projected to grow from 11.6 billion dollars in 2021 to 15.8 billion by 2026.
In the eyes of an ordinary layperson, the major source of sensitive information leaks are third parties. But in reality, it’s the opposite: the key threat is insiders. Moreover, the number of insider leaks has increased by 47 percent recently.
Companies use different approaches to information security to protect against insider threats, using technologies like information rights management, digital rights management, and data loss prevention. The more such protective means are introduced, the more attackers resort to workarounds like photos and screenshots. This leads companies to take new steps and look for new solutions.
But for now, back to insiders. How can you find out if they’re up to something?
Portrait of an Intruder
An offender can almost always be recognized by his inherent psychological characteristics, and his behavior and actions preceding the scam. This is a person who holds antisocial views and is guided primarily by selfish and possessive motives in his deeds. We can conditionally distinguish two groups of violators: cautious and careless.
Representatives of the first group are almost impossible to recognize. They take their time hatching their plan.
They are distinguished by:
· A low level of anxiety;
· An overly active desire to establish interpersonal contacts;
· Full social adaptability.
Representatives of the second group are the same lovers of “easy opportunities”.
They are characterized by:
· A high level of anxiety;
· Self-doubt;
· Irascibility and impulsiveness;
· A tendency to constantly blame others for their problems.
There are a few additional indicators that would suggest an insider threat:
· Staying in the office after business hours;
· Attempts to circumvent security;
· Use of unauthorized storage devices;
· Violation of corporate policy;
· Loading large amounts of data;
· Storing data and duplicating files from confidential folders.
Tips and Best Practices to Prevent Insider Threats
1. Provide Security Awareness Training
2. Enforce Security Policies and Create Social Media Guidelines
3. Implement Privileged Access Management Protocols
4. Implement Categorization to Minimize Risk
5. Conduct Proactive Network Monitoring
6. Use Geofencing and Time-fencing
7. Restrict Actions such as Copying or Transferring Sensitive Types of Files
What Tools Can Help You Deal With Document Leaks?
To deal with this problem, most companies use information rights management (IRM), digital rights management (DRM), and data loss prevention (DLP), which provide control over file access rights and actions. They also enrich documents with metadata and place them in crypto-containers, where access is granted only by permission.
But there is a problem here. These solutions are powerless when it comes to leakers photographing a document on a smartphone and compromising hard copies of documents. These solutions cannot cope with such leaks.
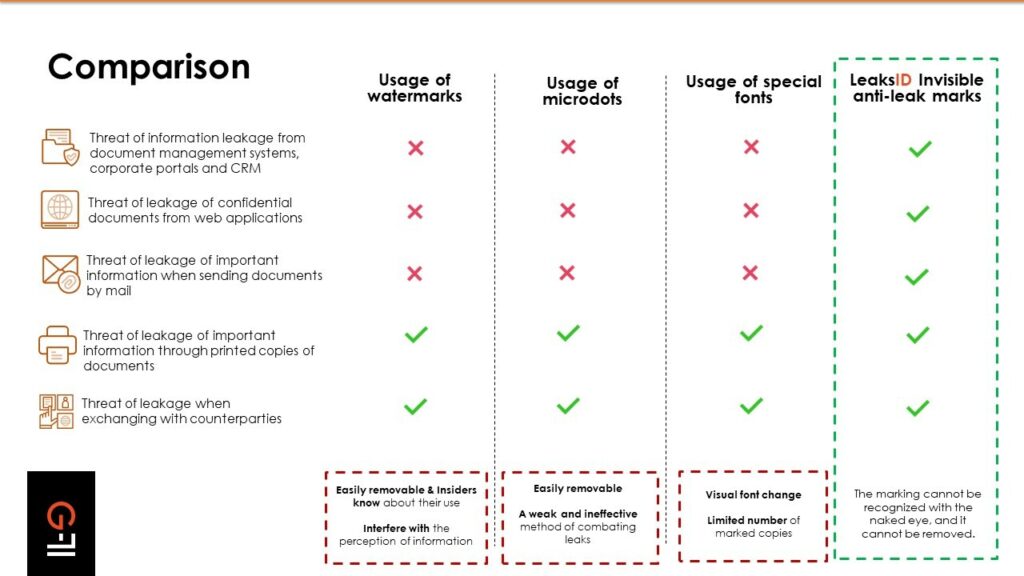
This security gap is partially closed by watermarks. They are simple, they are cheap to apply, and they can be dynamic. But they are visible, which means they can be easily removed. Here lies the main difference between watermarks and LeaksID technology by G-71: the system marks documents in an invisible way, and the marks cannot be recognized and removed. To remove the LeaksID marking, you must either delete all the text down to a blank sheet, or completely retype it in another document. But a fake document loses its value and takes on the form of gossip.
In addition, there are exotic ways besides watermarks. For example, the so-called yellow points (micro dots), where a small yellow dot is placed on a piece of paper. They are practically invisible. But unfortunately, if such a document is photographed, this dot will not be visible. In addition, they are not placed on the entire document, so part of the document remains unprotected.
Additionally, some use an unusual approach: special fonts. For example, special serifs are added to letters. Using this approach, you can create unique copies of documents, but there is a significant limit on the number of possible copies. When using the LeaksID solution, the patented labeling technology gives more variation, and creates over 205 trillion unique copies for one document.