Generally, virtual data rooms (VDR) are considered effective in protecting corporate information from external attacks and employee errors. However, they are practically helpless against insider threats armed with ordinary smartphones. Here is an overview of how LeaksID is solving this problem.
Most VDR suppliers offer extended security options to discover malware, restrict document viewing, encrypt files, and provide a multilevel system of access permission to sensitive data. These measures help to minimize the risk of data leakage.
The problem: Not all the risks covered
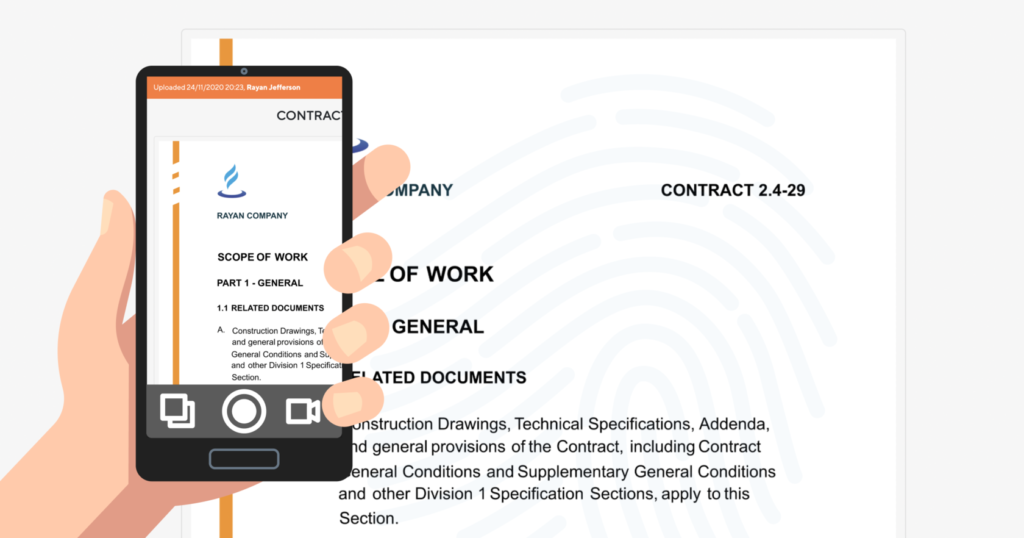
However, most VDRs are incapable of protecting one internal threat category: a data breach through screenshots, pictures of the screen, or printouts. Suppose an employee with file access wants to leak sensitive data. It can be done by simply taking a photo with a smartphone. By remaining unnoticed by security systems and leaving no traces in the future, it can be done again. Have you or your acquaintances been in situations when the secret information was published in the press or ended up in competitors’ hands, and the violator was never found?
The solution
Some VDR systems are trying to solve this problem by using popular watermark technology. However, watermarks can sometimes be removed manually, and the very concept is often inconvenient for the users. Perhaps you can recall situations when such marking made it difficult to perceive text and other visual information. How critical it is when dealing with official documentation and enormously expensive contracts!
We chose another way and developed LeaksID technology that includes all the necessary features of classic VDR and provides a new security level. How it works: When a file is uploaded to our secure storage, it is automatically replaced by a unique copy marked with special tags that are invisible to the user. These marks don’t interfere with work at all. If this file needs to be sent to another person, the system instantly generates a new copy with different tags. Using these tags, LeaksID can identify who worked with a particular file and when; if a data breach occurs, LeaksID can determine the source. The system works effectively even with screenshots and photos of the screen. LeaksID 100% guarantees the detection of a culprit; until recently, this was considered impossible.
LeaksID also has a preventive effect since all employees are aware that the company uses a solution that guarantees to find the culprit in case of an incident. As a result, employees are less likely to act illegally; therefore, in companies using LeaksID, the chances of a leak are minimized.
Who it is useful to
LeaksID technology can be especially useful to those who are involved in M&A transactions and audits, preparing for an IPO, working with confidential information, or protecting intellectual property, etc. In particular, the details of M&A transactions are kept secret until the last moment, and any data leak threatens to break the agreement. For instance, a few months before the merger of FanDuel and DraftKings, the news site Axios got a leaked copy of the document containing financial indicators, risks, the future company’s structure, and planned mass layoffs. This was one of the reasons why the transaction was canceled.
To minimize the chances of such incidents, many companies continue to integrate LeaksID technology into their infrastructure. Recently, we have also introduced team plans for the companies where several employees have access to sensitive data and work on the file in groups. For detailed information, follow the link.
Stay tuned!
Try out LeaksID, our cloud solution to store documents, collaborate on them, and securely share them.