Confidential Data Leaks: Who Steals and Why?

The motives for hacking, especially virtual hacking through penetration into the secret infrastructure of a company, are very diverse, as are the methods used for such purposes. Here are some examples of the most common reasons for theft.
Are DLP Systems the Best Solution for Leakage Prevention or Are There Better Ways to Protect Documents?

Documents continue to be compromised, companies are looking for countermeasures. One of them is DLP. But is this the best option?
How to Protect Your Business From Insider Threats

How can you find out if insiders are up to something? We in G-71 prepared a detailed analysis of how to identify an intruder. And prepared tips and best practices to prevent insider threats.
Recognized cybersecurity experts Brian DiPietro, Eric Seagren, and Jeff Reich joined the Advisory Board of G-71 Inc.

We’re delighted to share that Brian DiPietro, the former Chief Information Security Officer at JPMorgan Chase with over 16 years of experience, Eric Seagren, the Chief Information Security Officer at Oceaneering International, and Jeff Reich, the Co-Founder and Chief Risk Officer at LexAlign, joined the G-71 Board of Advisors. All three executives are exceptional leaders […]
How can you protect your quarterly reports, annual reports, and analytics from leaks?

Often, confidential information is leaked after you have given someone legal access to the document containing it. For example, say you work for a trading company and prepare an annual report presentation. You send it to trusted people, but in the end, one of them leaks the document. Who was it? It could be one […]
LeaksID (by G-71 Inc.) — a step towards a safer and more honest world

Where there is LeaksID, there is no place for criminal actions.
Black Friday Sale 2021

50% OFF
G-71 Inc. received a permanent US patent

On September 14, 2021, G-71 Inc. received a permanent US Patent No.11,120,520 B2.
How to Minimize VDR Security Risks with LeaksID
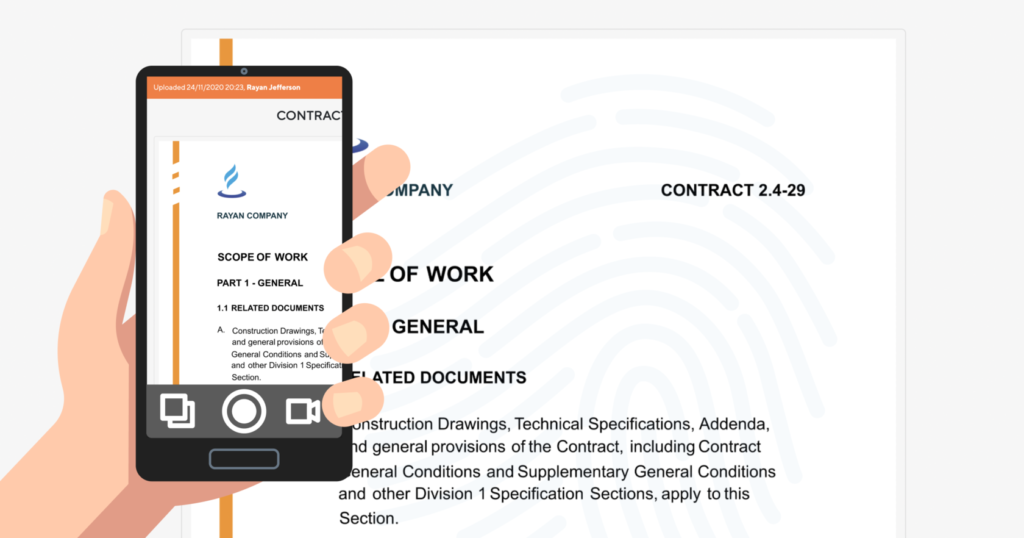
Here is an overview of how LeaksID is solving the problem of protecting corporate information from external attacks and employee errors.
Visible And Invisible: A Comparison Of LeaksID And Watermarks

This article will compare LeaksID and watermarks and find out the pros and cons of each technology.
